In this article, we are going to learn Identity and Access Management (IAM), AWS Roles/Permissions & How to give access to your AWS account to other users.
What is IAM?
AWS Identity and Access Management (IAM) is a web service that helps you securely control access to AWS resources. You use IAM to control who is authenticated (signed in) and authorized (has permissions) to use resources.
When you first create an AWS account, you begin with a single sign-in identity that has complete access to all AWS services and resources in the account. This identity is called the AWS account root user and is accessed by signing in with the email address and password that you used to create the account. We strongly recommend that you do not use the root user for your everyday tasks, even the administrative ones. Instead, adhere to the best practice of using the root user only to create your first IAM user. Then securely lock away the root user credentials and use them to perform only a few account and service management tasks.
IAM features:
- Shared access to your AWS account
- Granular permissions
- Secure access to AWS resources for applications that run on Amazon EC2
- Multi-factor authentication (MFA)
- Identity federation
- Identity information for assurance
- PCI DSS Compliance
- Integrated with many AWS services
- Eventually Consistent
- Free to use
Accessing IAM:
You can work with AWS Identity and Access Management in any of the following ways.
- AWS Management Console
- AWS Command Line Tools
- AWS SDKs
- IAM HTTPS API
Creating an IAM user in your AWS account:
- Sign in to the AWS Management Console and search the IAM console search tab.
- In the navigation pane, choose Users and then choose Add users.
Set User Details:
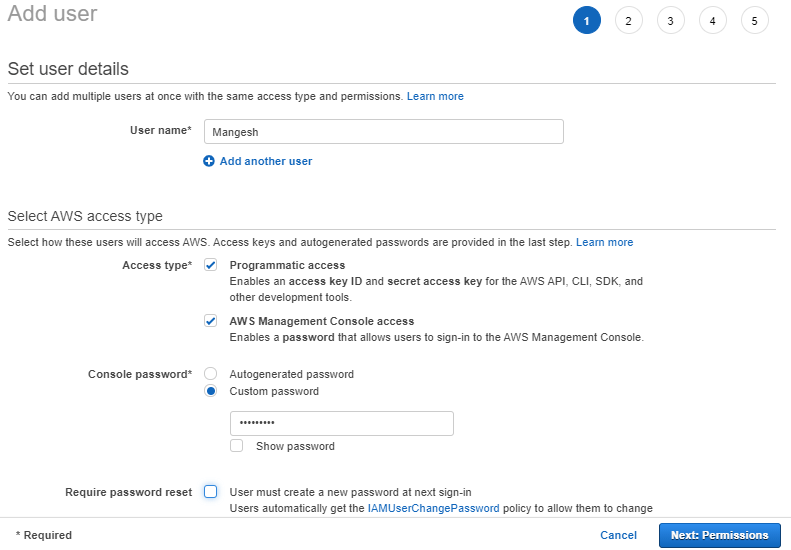
Type the user name for the new user. This is the sign-in name for AWS. If you want to add multiple users, choose to Add another user for each additional user and type their user names. You can add up to 10 users at one time.
Note: The number and size of IAM resources in an AWS account are limited. For more information, see IAM and AWS STS quotas. User names can be a combination of up to 64 letters, digits, and these characters: plus (+), equal (=), comma (,), period (.), at sign (@), underscore (_), and hyphen (-). Names must be unique within an account. They are not distinguished by case. For example, you cannot create two users named TESTUSER and testuser.
Select the type of access this set of users will have. You can select programmatic access, access to the AWS Management Console, or both.
- Select Programmatic access if the users require access to the API, AWS CLI, or Tools for Windows PowerShell. This creates an access key for each new user. You can view or download the access keys when you get to the Final page.
- Select AWS Management Console access if the users require access to the AWS Management Console. This creates a password for each new user.
For Console password, choose one of the following:
- Autogenerated password. Each user gets a randomly generated password that meets the account password policy. You can view or download the passwords when you get to the Final page.
- Custom password. Each user is assigned the password that you type in the box.
(Optional) We recommend that you select Require password reset to ensure that users are forced to change their password the first time they sign in.
Note: If an administrator has enabled the Allow users to change their own password account password policy setting, then this check box does nothing. Otherwise, it automatically attaches an AWS-managed policy named IAMUserChangePassword to the new users. The policy grants them permission to change their own passwords.
Choose Next: Permissions.

Set permissions:
On the Set permissions page, specify how you want to assign permissions to this set of new users. Choose one of the following three options:
- Add user to group
- Copy permissions from an existing user
- Attach existing policies directly
(Optional) Set a permissions boundary. This is an advanced feature,
Here I will select the “AdministratorAccess” policy in the “Attach existing policies directly” option, then Choose Next: Tags.

Add tags (optional):
IAM tags are key-value pairs you can add to your user. Tags can include user information, such as an email address, or can be descriptive, such as a job title. You can use the tags to organize, track, or control access for this user.
Choose Next: Review to see all of the choices you made up to this point. When you are ready to proceed, choose to Create user.
Review:
Review your choices. After you create the user, you can view and download the autogenerated password and access key.

To view the users’ access keys (access key IDs and secret access keys), choose Show next to each password and access key that you want to see. To save the access keys, choose Download .csv and then save the file to a safe location.
Important: This is your only opportunity to view or download the secret access keys, and you must provide this information to your users before they can use the AWS API. Save the user’s new access key ID and secret access key in a safe and secure place. You will not have access to the secret keys again after this step.
Provide each user with his or her credentials. On the final page, you can choose to Send an email next to each user. Your local mail client opens with a draft that you can customize and send. The email template includes the following details for each user:
- User name
- URL to the account sign-in page. Use the following example, substituting the correct account ID number or account alias:
https://AWS-account-ID or alias.signin.aws.amazon.com/console
No w you can see, The user has been successfully created.

That’s all, In this article, we have explained How to create AWS IAM User? AWS Identity and Access Management (IAM). If you like this article, then just share it and then do subscribe to email alerts for Linux, Windows, macOS, Android, Internet, Firewall and Security, CCTV tutorials. If you have any questions or doubts about this article, please comment.